You may have noticed the new subtab under the Compliance tab in your lead system. This is our new Security Hub! The Security Hub is a dashboard where admins can review security related activity, stats and recommendations all in one place. Each dashboard module can be expanded to show more information/details or link directly to the relevant configuration page.
When you first enter the Security Hub, you will see Lead System Users, API Key Security, Two-Factor Authentication Adoption and User Activity Log. Each of these adds an extra layer of visibility to system and data security and are easy to access from this single subtab.
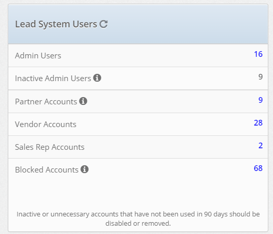
Lead System Users
This section shows all of your users by groups in one standard place. You can select the number and have a new tab open that shows users of that type. This includes admins, partners, vendors and more. You can even see what accounts have been blocked from here as well! Pro Tip: Any users who are considered Inactive or Unnecessary should be disabled or removed. You can monitor that from the Inactive Admin Users count.
API Key Security
Think of API Keys as the combination to a safe with some of your valuables in it. Only trusted users should know or have access to it. Luckily, unlike safe combinations, you can restrict who has access to your API Key even if they know the "combination." These restrictions can be based on geography or by IP address.
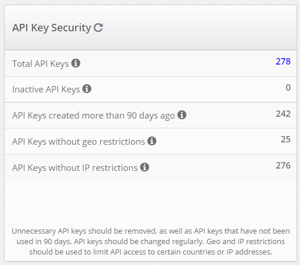
Even if API Keys are not used for a while, they should not be forgotten; they can still be accessed. The API Key Security section allows users to see how many API Keys they have active, how many are "inactive" (have not been used for 90 days), ones that were created more than 90 days ago, and how many have either geographical or IP address restrictions. To stay as secure as you can with API Keys, it is a good practice to delete inactive API Keys and change or delete ones that were created more than 90 days ago. Be sure to add geo and IP restrictions to as many keys as you can as well.
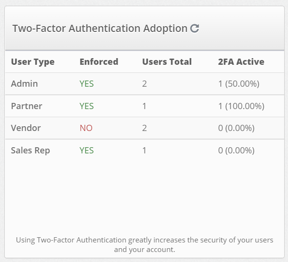
Two-Factor Authentication Adoption
So many apps and software have 2FA enabled in their products. Why? Because it is one of the easiest and most effective ways to secure your account and data. This section is to monitor how many of your users have 2FA enabled with their account. The 2FA Active section should be at 100% of users across the board. You can see who has 2FA enabled under the Lead System Users section by clicking on the related number. 2FA can be enforced at the system level which will require users to provide the 2FA token before gaining access to other areas of the system. Contact customer support if you need to change 2FA enforcement settings.
User Activity Log
This section is where you can see all the activity for everyone that logs into your lead system. You can search for specific users or filter by ID, date created, IP address or the specific page they were on. This is a good way to monitor your users and what they are doing. If anything odd is happening, you can see what changes were made and by whom right from here.
You can also run a Report in the reports tab called Activity by Hour to get a breakdown of user activity for a certain day. This can even be set up as a timed report if you would like to get a daily or weekly summary. Otherwise, going to the Tools/Logs tab, you can see all user activity for the last 12 hours.
To learn more about boberdoo security, check out the aptly named Security section of our website. We also have a dedicated blog section regarding system and data security, as well as our privacy policy. We have a webinar you can watch dedicated to boberdoo's Information Security Program. If you have any questions, do not hesitate to reach out


