The snow is disappearing and the warm weather is returning! Time for cookouts, t-shirts and spring cleaning, not only for your home but for your system as well! Here is our checklist to keep your system clean and secure!
1. Organize Group Permissions
Keep things together, right? Just as you would organize your sock drawer, each user group should only be granted permissions that match the requirements of their role. Find out more about how to set permissions and get tips for who should be allowed to see what.
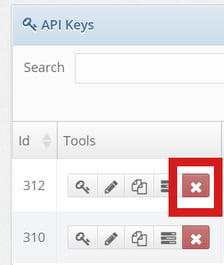
2. Toss Out Old Users & API Keys
Do these users spark joy? If not, toss them out like old clothes or knick-knacks. Those old admins, partners, vendors and API keys are better out of your system than in. Find out more about how to delete or change API Keys and keep them on a need-to-know basis. Delete or suspend old users you do not use anymore, even if there is a chance you may need them in the future. You can always create a new user. Stale users that just sit there are bad for business.
3. Check Your Compliance & Retention Settings
Checking these settings is similar to but much more pleasant than cleaning out the refrigerator. With both, anything expired has to go. Only keep information that is needed, and house your data in a secure location. Refrigeration not required! Learn more about different options for data like using Amazon S3.
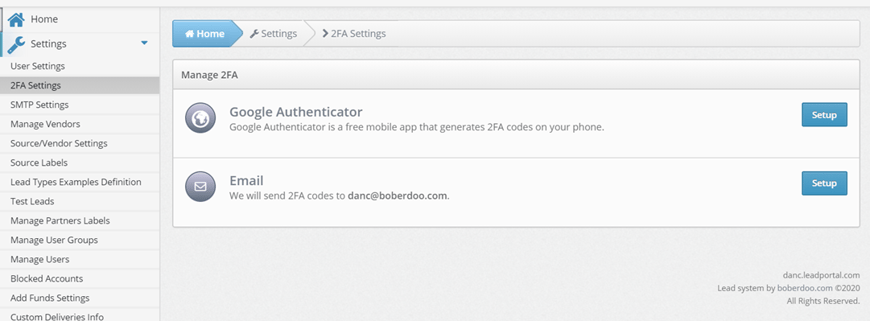
4. Lock It Down With 2-Factor Authentication
Your front door has a lock, no doubt. Most have a combination of deadbolts, chains, and door knobs with locks, perhaps even a camera and alarm as well. Just as with doors, take more than one precaution with your system. Setting up 2FA keeps valuable data and settings more secure than a password alone. Protect your data like you protect your home.
5. Only Give Keys To The People You Want In
Dorm rooms may have open door days, but our system does not. Setting up Geo (good) and/or IP restrictions (better) will only allow users from your areas or specific IPs to log in.
6. Always Be Aware When Something Is Out Of Place
We have all been there, "Dear have you seen my wallet, keys, phone, etc." When something is out of place or something out of the ordinary is happening, find out instantly with webhooks and notifications. These can be used for security measures such as account lockouts and data exports.


